Two-factor authentication
Fintech is great—end users love and expect it. But it has blown the doors of opportunity open for cyber criminals. Just because someone knows a valid username and password doesn’t mean they are who they say they are. According to Verizon’s 2018 Data Breach Investigations Report, guessed or stolen credentials was the top tactic for data breaches.
To mitigate the threat of guessed or stolen credentials, Banno requires two-factor authentication (2FA) for three scenarios:
- It’s the end user’s first time interfacing with your app.
- A new device is being used to access bank accounts.
- The end user recovering their account.
Setting up 2FA
To get started on the Banno platform, new users log in, and mobile users will choose a PIN for quick account access in the future. This login process establishes their first authentication factor: something they know (their credentials) or something they are (like a fingerprint).
Wonder how new users get their credentials?
- Create a new account using their personal identifiable information;
- Carry over their username and password associated with your current online banking solution;
- Receive a username and temporary password issued by you, the FI.
Then, they will designate their second authentication factor: something they have (like a phone).
First time setup for end users without 2FA
When an end user attempts to use the app without 2FA configured while your institution has 2FA enabled, an additional layer of security is required before choosing and configuring a 2FA method.
After entering their username and password, the end user is sent an email containing a verification that must be entered into the app before they can continue with 2FA configuration. After the verification code is confirmed, the end user can continue to the 2FA method configuration outlined below. They are then required to verify their configured 2FA method before accessing their account.
2FA support for international end users
End users can receive 2FA sign-in codes via international phone numbers; however, they cannot use an international number for the initial 2FA enrollment validation. Therefore, before we can enable 2FA support for international numbers, you’ll need to work with your Banno implementation coordinator or support rep to establish 2FA enrollment validation via email rather than via core validation. This change—which only affects the one-time validation step users complete during 2FA enrollment—is required due to known limitations that prevent Banno from validating international phone numbers against the core.
To support 2FA via international phone numbers, ask your implementation coordinator (or Banno Support) to get the ball rolling. Once we’ve completed the changes, any end user who enrolls in 2FA will be prompted to validate their enrollment via email. This applies to end users with US-based phone numbers as well. If you later decide that email validation isn’t right for your institution, an authorized employee can always revert the changes in People (though, we highly recommend reaching out to Banno Support beforehand with any questions regarding the impact on end users).
2FA verification methods
There are plenty of ways an end user can prove who they are, and secure new methods are being developed all the time. To ensure there are as few barriers as possible to utilizing the security of 2FA, Banno maintains a growing list of 2FA authentication options for end users to choose from and for you to control. No matter what kind of person the end user is, we make sure they can enroll in 2FA.
Banno apps offer the following methods of 2FA authentication for end users and can be managed by your institution in Banno People.
- Settings
- 2-step verification
If an end user is unable to receive a 2FA code, commonly they’ll receive the error warning Your 2FA code failed to deliver to your default method. Please try another way. and be prompted to verify the code delivery again. In the Verification code delivery window, they can choose from other delivery methods set within their account.
Authy
Banno natively supports the Authy authenticator app. The end user provides an email address and phone number associated with account. When performing an action that requires 2FA authentication, the end user can copy their authentication code directly from the Authy app.
Your institution can decide whether or not to validate the provided phone number against your core records. If this is enabled, the end user must enter a phone number you have on file for that user. Users without a correct phone number will not be able to successfully enroll. After a user enrolls, they can change the phone number inside the Authy authenticator app to a different number.
Phone or text message
The end user provides a phone number to validate with, selecting to receive authentication codes via text message or automated phone call. When performing an action that requires 2FA authentication, the end user receives a text message or phone call containing a code to enter into their Banno app.
Your institution can decide whether or not to validate the provided phone number against your core records. If this is enabled, the end user must enter a phone number you have on file for that user. End users without a correct phone number will be unable to successfully enroll.
Authenticator app
Banno supports non-Authy authenticator apps for end users who cannot access Authy, or who simply prefer another authenticator app. The Banno app provides a text code, as well as a QR code for desktop users, to enter into their chosen authenticator app. The end user can then use their chosen app according to its documentation.
FIDO security keys
The FIDO security key is a physical token that connects to the end user’s computer via USB, Bluetooth, or NFC. The authenticator code is automatically entered and never shared with anyone, including the end user utilizing the key.
Symantec hardware/software tokens
Banno supports Symantec VIP tokens as either a hard or soft token. The end user provides their credential ID and then validates the 2FA code based on that credential when enrolling. When logging in, the end user provides the code as requested to access Banno.
Short codes
When it comes to end users receiving 2FA codes via voice or text message, short codes for 2FA provide an option not affected by carrier rate limits. This is great news for end users, as they promptly receive their 2FA codes and aren’t subject to stalled or undelivered codes! With short codes enabled, users receive their 2FA codes via Banno’s unique short code number—53286. All Banno institutions use the same short code number, and institution-specific short codes are not supported.
Short codes are used to deliver 2FA codes as SMS texts. Short codes cannot receive messages for any of the following:
- 2FA codes delivered by phone call, although if it’s detected that a phone number doesn’t accept SMS (a landline for example), a phone call will automatically send
- 2FA codes generated in Authy
- 2FA codes generated in any other authenticator apps
- In-app alerts
- Messages (including scheduled Messages) that an institution admin creates in People for distribution to all end users
- Conversations and related alerts
- Any other in-app alert in Banno
- 2FA codes delivered to international numbers
Configure
Short codes are enabled by default and cannot be disabled.
SMS messages
End users can receive the following SMS messages via the short code number:
Security code message
After tapping or clicking Send code in the Banno app, end users receive this message: [Institution name] security code: [unique-2FA-code] We will never ask for this code—don’t share it. [combination of characters] [hyperlinked unique-2FA-code]
The combination of characters (ex. m1BEiLPED7j@accounts.myinstitution.bank) and hyperlinked unique-2FA-code at the bottom of the SMS message is used for browser autofill features and designates the website it is allowed to be used on.
Opt out reply
If an end user texts STOP, CANCEL, END, QUIT, STOPALL, or UNSUBSCRIBE to the short code number, they receive this reply: You won’t receive additional SMS messages from your financial institution regarding your 2FA security code. To re-enroll at any point, text START. Msg and data rates may apply. 1msg/access.
Opt in reply
If a user texts START or UNSTOP to the short code number, they receive this reply: You have been re-enrolled to receive SMS messages fro your financial institution regarding your 2FA security code. Msg and data rates may apply. 1msg/access. Reply HELP for help and STOP to stop receiving these messages.
Help reply
If a user texts HELP or INFO to the short code number, they receive this reply: 2FA Security Code Messages: Please contact your financial institution for help signing in. You may also call or text 1-888-291-9631 Msg and data rates may apply. 1msg/access. Reply HELP for help and STOP to stop receiving these messages.
All messages sent
The short code only receives messages strictly related to Banno 2FA codes; no other communications, alerts, or messages will be sent via the short code.
Change Banno Apps settings
- Settings
- Security
- 2-step verification
If an end user wants to change their 2FA settings in Banno Apps, the security menu allows users to edit their existing 2FA methods or add a new one. End users can also set a primary 2FA method that will be automatically highlighted whenever they receive a 2FA authentication prompt.
Change Enterprise settings
Within Banno Enterprise, you can control your institution’s 2FA verification methods in Banno People. You can also change 2FA settings on behalf of individual end users in their Security settings.
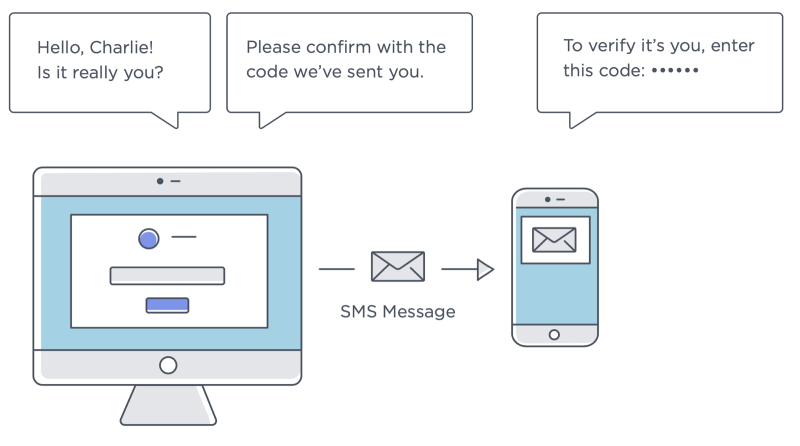
New device: Prove a user’s identity
Banno keeps tabs on the devices and browsers that are logging into user accounts by using device IDs1 and browser fingerprinting2. Whenever an end user attempts to login on a device that the API doesn’t recognize, they will be asked to prove their identity using 2FA. It’s just another security measure taken to protect the end user in the even that their credentials are compromised.
Banno Enterprise
Within Banno Enterprise, you can control your institution’s and end users’ 2FA settings. Because we consider changing 2FA options a high-risk change, an enterprise user will need to be in a group with 2FA enabled.
FAQ
- Can an end user’s 2FA phone number be provided upon request?
- For the user’s security, an end user’s phone number is hashed across all platforms and cannot be provided.
- Can we override the institution’s 2FA setting for specific end users?
- Yes! To change settings for a specific end user, navigate to the Security page for that end user.
- Can we have an institution-specific 2FA short code number?
- No, institution-specific short codes aren’t supported.
- On some SMS 2FA codes, what’s the email address (ex. @online.tx.org) that displays?
- Actually, this isn’t an email address but an an App hash. While the majority of devices don’t use an App hash, certain ones use it as part of 2FA and generating one-time codes sent by SMS. This allows us to support a higher number of different devices used by end users. You can checkout WebOTP API for more information on generating a one-time password (OTP).
- How can we support an end user who is unable to use a phone for verification?
- End users that for any reason are unable to use a phone for two factor authentication may use the Authy app to authenticate. Setup requires use of a phone, so assisting with initial setup should be supported at your institution’s local branches in case an end user is unable to gain assistance from a friend or family member. After initial setup, Authy allows authentication without use of a phone.
- Can we enable 2FA over email?
- If you want to enable 2FA over email, you will need to open a case with our support team and sign a waiver of liability.
-
Device ID: A unique ID is issued to a device with every installation of Banno Mobile. That ID is presented with every login as a way for the system to associate the device with an authenticated user. ↩︎
-
Browser fingerprinting: A method used to collect information about a user, like their operating system, language, and various other active settings. ↩︎